Demonstrating Symmetric Encryption Using Photoshop®
Nov 23, 2009 by Bill Soley
Brief Introduction to Encryption Terminology
"In cryptography, encryption is the
process of transforming information (referred to as plaintext)
using an algorithm (called cipher)
to make it unreadable to anyone except those possessing special
knowledge, usually referred to as a key. The result of the
process is encrypted information ([...] referred to
as ciphertext)." (wikipedia)
We will use the symbol p for the
plaintext, ⊕
for the cipher operation, k
for the key, and c
for the ciphertext. The ⊕
symbol is commonly used to denote boolean exclusive-or, which happens
to be the cipher operation chosen for our demonstration. All together
we can write the encryption
operation as ...
... which we would read as "plaintext p is encrypted with
key k
producing ciphertext c."
The process of turning the ciphertext back into the plaintext
is called
decryption.
A good cipher only allows decryption by those that know the
key. In our demonstration, the operation to decrypt is the same as the
operation to encrypt, so we will use the same symbol, ⊕
as we did for encryption. Also, since our example uses a symmetric
cipher, the key used to decrypt is the same as the key used to encrypt,
so will will use the same symbol, k,
for that, too. Decryption can then be written as ...
... which we would read as "ciphertext c is decrypted with
key k
producing plaintext p."
Typical Use Case
If Alice wants to send a secret message, p, to Bob, then
Alice and Bob must first agree on a key, k, which they must
keep secret.
| (3) |
Alice: |
knows
k |
|
Bob: |
knows
k |
Once Alice knows the key, k, she
can encrypt her message plaintext, p,
to create the ciphertext, c.
Alice then sends the ciphertext, c, to Bob. It does
not matter if anyone else sees the ciphertext on its way to Bob because
only Alice and Bob know the key, so they are the only ones that can
decrypt the ciphertext.
Once Bob receives the ciphertext, c, since Bob already
knows
the key, k,
he may decrypt the message.
Alice has successfully used encryption to send a message, p, to Bob while
keeping the contents of the message private even though there may be
evesdroppers (in step 5) that can see the ciphertext, c, as it is being
delivered to Bob.
Exclusive-or
Cipher
The cipher we will be using in our demonstration is based on
the
exclusive-or operator, abbreviated as xor (pronounced like ecks-ore).
The most common mathematical symbol for the exclusive-or operation is
⊕.
This operator is boolean (or logical) operation, which
means
it operates in the domain of true and false (or 1 and 0). The result
of ⊕
is 1 only if one of its inputs is 1,
but not both.
In other words, the output is 1 unless both inputs are the same. Here
is a truth table for exclusive-or ...
| (7) |
inputs |
output |
|
0 ⊕ 0
|
= 0
|
|
0 ⊕ 1
|
= 1
|
|
1 ⊕ 0
|
= 1
|
|
1 ⊕ 1
|
= 0
|
Some facts about exclusive-or:
| (8a) |
a ⊕ b
|
=
|
b ⊕ a
|
|
(commutative) |
| (8b) |
(a ⊕ b) ⊕ c
|
=
|
a ⊕ (b ⊕ c)
|
|
(associative) |
| (8c) |
a ⊕ a
a
|
=
=
|
0
0 ⊕ a
|
|
(identity) |
| (8d) |
a ⊕ ¬a
¬a
|
=
=
|
1
1 ⊕ a
|
|
(inverse) |
The key will be a randomly chosen string the same length as
the plaintext. This technique is called a one time pad. It is very
simple, so it makes a good demonstration. In spite of its simplicity it
can be perfectly secure under the proper conditions. As long as the key
is kept secret and the same key is never
used for more than one message, then the one time pad is the only known
provably secure cipher.
Simulating Exclusive-or in Photoshop
 This demonstration uses images manipulated in the Adobe
Photoshop®
program.
While Photoshop does not directly support blending images using
exclusive-or, it does support a function, which it calls difference,
that is close enough to use for this demonstration.
This demonstration uses images manipulated in the Adobe
Photoshop®
program.
While Photoshop does not directly support blending images using
exclusive-or, it does support a function, which it calls difference,
that is close enough to use for this demonstration.
Warning:
The difference
operation behaves exactly like exclusive-or only as long as the images
being blended contain only the basic eight colors: black, red, yellow,
green, cyan, blue, magenta, and white. If the images contain any other
hues or shades then the function does not behave like exclusive-or and
the demonstration will fail. We must therefore carefully make
sure
that only the basic colors are present.
The
chart at left shows a truth table for the Photoshop difference
operation over the basic eight color domain. The rows and columns
represent the
inputs to the difference function, and the corresponding square in the
grid shows the output for the given pair of inputs. For example, follow
the yellow (Y) row, and the cyan (C)
column, to see magenta for the result:
| (9) |
yellow ⊕ cyan = magenta
|
Notice that each row and column in the truth table contains
each and every color
exactly
once. This is an important property if the function is to be used for
encryption. Without this property, more than one plaintext message
could encrypt to the same ciphertext thereby making decryption
impossible because there would be no way to know which of the possible
plaintexts was correct.
Another noteworthy property is that you can undo an exclusive-or operation by repeating it. For example, yellow (Y) ⊕ red (R) = green (G) and green (G) ⊕
red (R) = yellow (Y). You can see why from (8c) above. This property
allows us to use the same operation to encrypt and decrypt.
 To
invoke the difference function in Photoshop, place each image in a
separate layer with layer blending mode to difference. The
blending mode appears in a pull-down control that Photoshop initializes
to normal
when a new layer is created. (See the screen shot on right.) The
blending mode must be set separately for each layer by selecting the
layer and then selecting difference
in the pull-down control.
To
invoke the difference function in Photoshop, place each image in a
separate layer with layer blending mode to difference. The
blending mode appears in a pull-down control that Photoshop initializes
to normal
when a new layer is created. (See the screen shot on right.) The
blending mode must be set separately for each layer by selecting the
layer and then selecting difference
in the pull-down control.
Once the blending mode has been set to difference, you may
enable and disable individual layers by clicking on the eye
icon next to each layer. Photoshop will display the exclusive-or of all
enabled layers.
Details of Layer Blending
You may skip this section unless you are particularly curious
about how colors are represented and blended in Photoshop.
Each image of the type we are using for this demo is
represented by three channels: red, green, and blue. This is commonly
called an RGB image. The three channels represent the primary
colors of light for humans and by adding them together in various
proportions we can make any color. (Many people were taught the RYB color
model based on red, yellow, and blue "primary" colors,
however, RYB, as well as the more accurate CMY, are actually
subtractive colors used for blending pigments or dyes and are do not
apply when blending light.)
An image in Photoshop is made up of rows and columns of dots
called pixels. Ideally these pixels are spaced so close together that
they are not individually visible. Each pixel in the image has a
numeric value for each channel. In our case that
value is in the range 0 to 255, where 0 means no light for that color
channel, and 255 means full brightness. For xample, if a particular
pixel is yellow (red + green = yellow), it would have a red
value of 255, a green value of 255, and a blue value of 0.
For this demonstration, we are interested in the difference blending
function. Although we are using it to approximate exclusive-or, the
actual function used by Photoshop is the absolute value of the
difference of the two channel values.
| (10) |
Difference(a,b) := |a-b|
|
The eight basic colors: black, red, yellow,
green, cyan, blue, magenta, and white, have RGB channel values
consisting of 0 and 255 only. Notice that if the domain of
the channel values is limited to 0 and 255, then the result of the
Photoshop difference
operation is identical to exclusive-or.
| (11) |
|a-b| =
a⊕b, for a,b∈{0,255}
|
If Photoshop had an exclusive-or blending function, then we
could use ordinary digital photo images in the demo. However, due to
only having the difference operation, we are forced to use line art
with a pallete limited to the eight basic colors. The image in
the examples, below, is an artistic sketch of me using only the eight
basic colors.
Simulating the Encryption and Decryption
For this demonstration, I have chosen an artistic sketch of
myself, which you can see, below, labeled plaintext. Once we
have chosen the plaintext image, we create a key image that has the
same dimensions as the plaintext image. The key image gets filled with
random noise using the eight basic color pallete. You can see the one I
created,
below, labeled key.
The next step is to import both images into Photoshop as layers and set
the layer blending mode to difference.
With both layers enabled, Photoshop will compute the blended image
using our exclusive-or cipher and display the ciphertext on
the screen. You can save the ciphertext to a file with layers merged.
|
original
plaintext |
|
key |
|
ciphertext |
|
|
| Alice: |
 |
⊕
|
 |
=
|
 |
|
|
|
|
|
↓ |
key shared via
secure channel |
|
↓ |
message sent via
insecure channel |
|
reconstructed
plaintext |
| Bob: |
|
|
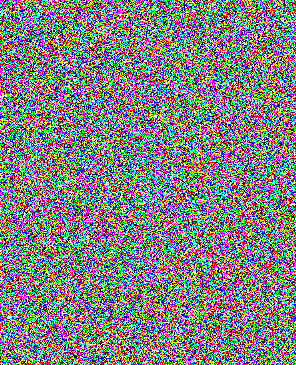 |
⊕
|
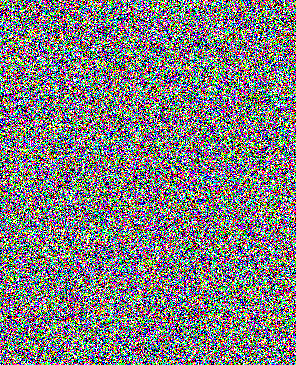 |
= |
 |
You can right-click on each image, above, and save them to a
file, then import the files into Photoshop as separate layers. To save
you some work, you may download
a Photoshop file with the layers already imported. Either way, to view
the encryption and decryption, make sure all the layers have their
blending mode set to difference,
then enable one or two layers at a time. The following table describes
what you should see with various combinations of layers enabled:
|
plaintext
layer |
key
layer |
ciphertext
layer |
description |
|
X |
|
|
original
plaintext sketch of me |
|
|
X |
|
randomly
generated key |
|
|
|
X |
ciphertext
that Alice sent to Bob |
|
X |
X |
|
result
of encryption |
|
|
X |
X |
result
of decryption |
Creating Your Own Plaintext
Given that the demonstration uses the difference
function, which approximates exclusive-or only when the pallete is
limited to the eight basic colors, one is likely to need to transform a
source image into some form meeting the color pallete requirement. The
following steps may be followed to transform an ordinary photograph
into a suitable line drawing with the appropriate color pallete.
- File→Open... (select file), [OK]
- crop photograph if desired
- Filter→Stylize→Glowing Edges..., adjust sliders to taste, [OK]
- Image→Adjustments→Posterize..., levels=2, [OK]
- Image→Adjustments→Invert (optional)
- File→Save As..., save as=plaintext.png, format=PNG, [Save]
- File→Close All, [Don't Save]
You may have to play with the choice of filters and parameters in step 3 and repeat steps 3-5 to find results you like.
Creating Your Own Key
For a one time pad using exclusive-or, we simply need a random
key the same length as the plaintext. Before creating the key, check
the size of the image you wish to use as plaintext. The image I used in
this example is 296 pixels wide, by 365 pixels high. Create
a new image having the same dimensions as the plaintext image and fill
it with random noise from our eight basic color pallete. We will use
this image as our key.
- File→New..., name: key, width=296, height=365, resolution=100 pixels/inch, color mode=RGB 8-bit, [OK]
- double-click on foreground color to open color chooser, set R=128, G=128, B=128, [OK]
- select paint bucket tool
- click within the canvas to fill with 50% grey
- Filter→Noise→Add Noise..., amount=50%, distribution=Unifrm,
 Monochromatic, [OK]
Monochromatic, [OK]
- Image→Adjustments→Posterize..., levels=2, [OK]
- File→Save As..., save as=key.png, format=PNG, [Save]
- File→Close All, [Don't Save]
Step 5 uses the internal Photoshop random number generator to
generate random pixel values. Note that the random number source in
Photoshop is not truely random and contains patterns and artifacts that
might make the ciphertext easier to cryptanalyze. That's fine for a
demo, but any serious use should utilize a cryptographic grade random
number source.
Creating Your Own Ciphertext
In order to create your own ciphertext file by encrypting your
plaintext file with your key, you must import the plaintext image and
the key image into Photoshop as separate layers. Then set the layer
blending mode to Difference. You can then save the result as a
ciphertext file.
- File→Open..., plaintext.png, [OK]
- File→Open..., key.png, [OK]
- Select→All
- Edit→Copy
- Window→plaintext.png
- Edit→Paste
- Layer→Layer Style→Blending Options..., Blend Mode=Difference, [OK]
- File→Save As..., save as=ciphertext.png, format=PNG, [OK]
- File→Close All, [Don't Save]
Decrypting Your Own Ciphertext
In order to decrypt your own
ciphertext file using your key, you
must import the ciphertext image and the key image into Photoshop as
separate layers. Then set the layer blending mode to Difference.
- File→Open..., ciphertext.png, [OK]
- File→Open..., key.png, [OK]
- Select→All
- Edit→Copy
- Window→ciphertext.png
- Edit→Paste
- Layer→Layer Style→Blending Options..., Blend Mode=Difference, [OK]
- the image on the display should match the original plaintext
- File→Close All, [Don't Save]
Creating a Duress Key
The cipher used in this demo has the property that there exists a
key that will decrypt any ciphertext into any plaintext of the same
size. This is not a common property of modern ciphers, but it is a
feature of the one time pad. In fact this property is the basis of a
proof that the one time pad provides perfect privacy. The proof
basically reasons that if there is a key that can transform a given
ciphertext into any plaintext of the same size, then without knowing
the original key, it is impossible to know which of the possible
plaintexts of the same size is the true original plaintext.
We can take advantage of this property to create a duress key. This
key would be created and kept by Alice or Bob in case some malevolent
party attempts to coerce Alice or Bob to decrypt the plaintext by
threating, for example, bodily harm. This technique is commonly called rubber-hose cryptanalysis.
To create the duress key, we first need a decoy plaintext image, and
the actual ciphertext. Follow the same steps described in Creating Your Own Plaintext to create a decoy plaintext, but save the file as decoy.png. The decoy plaintext must be the same size as the real plaintext.
- File→Open..., ciphertext.png, [OK]
- File→Open..., decoy.png, [OK]
- Select→All
- Edit→Copy
- Window→ciphertext.png
- Edit→Paste
- Layer→Layer Style→Blending Options..., Blend Mode=Difference, [OK]
- File→Save As..., save as=duress_key.png, format=PNG, [OK]
- File→Close All, [Don't Save]
Now if you become the subject of coercion, from Mallory, you can
give her your duress key. When Mallory decrypts the captured ciphertext
using the key you supplied, she will see only the decoy image. You may
feel a momentary smugness for having defeated your adversary, however,
a serious problem with this situation is that if Mallory is not
impressed with the decoy image and suspects it might be a decoy then
she may increase the level of coercion in an attempt to get the real
key. You might counter this by having multiple decoy images with
multiple duress keys. Even when you reach your limit and decide to give
Mallory the real key, she may still continue to apply increasing levels
of coercion unless it is certain and obvious that you are not still
holding out. Indeed you may put yourself in this position by using a
cipher that supports duress keys even if you choose not to create one.
|
original
plaintext |
|
key |
|
ciphertext |
|
|
|
|
|
| Alice: |
 |
⊕
|
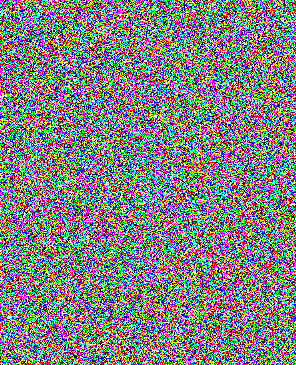 |
=
|
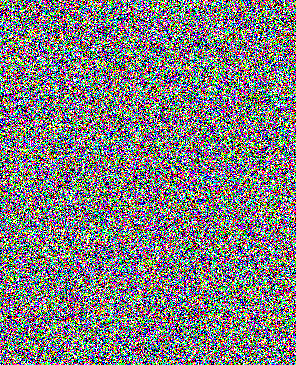 |
|
|
|
|
|
|
|
|
decoy
plaintext |
|
↓ |
copy of
ciphertext
|
|
duress
key |
|
|
| Alice: |
|
|
 |
⊕
|
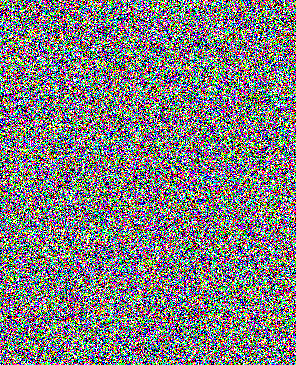 |
= |
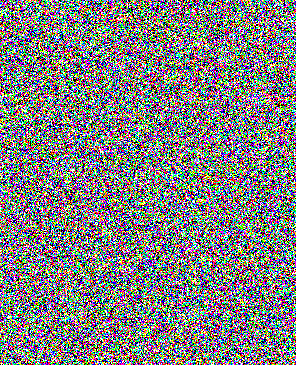
|
|
|
|
|
|
|
|
|
↓ |
captured
ciphertext |
|
↓ |
key obtained
by coercion |
|
reconstructed
decoy |
| Mallory: |
|
|
|
|
|
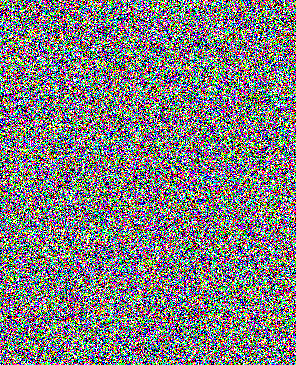 |
⊕
|
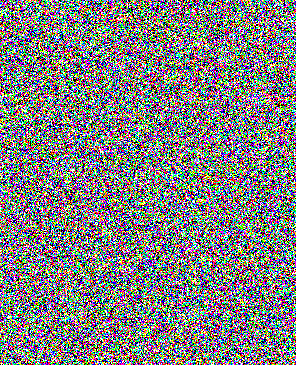 |
= |
 |
You can right-click on each image, above, and save them to a
file, then import the files into Photoshop as separate layers. To save
you some work, you may download
a Photoshop file with the layers already imported.
 This demonstration uses images manipulated in the Adobe
Photoshop®
program.
While Photoshop does not directly support blending images using
exclusive-or, it does support a function, which it calls difference,
that is close enough to use for this demonstration.
This demonstration uses images manipulated in the Adobe
Photoshop®
program.
While Photoshop does not directly support blending images using
exclusive-or, it does support a function, which it calls difference,
that is close enough to use for this demonstration. To
invoke the
To
invoke the 
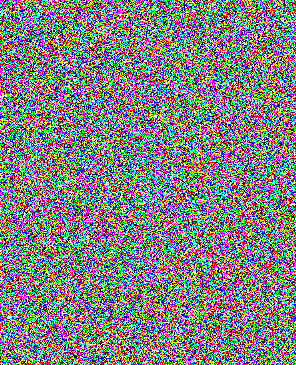
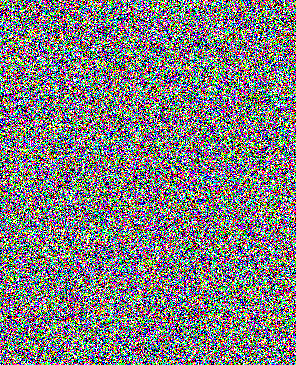
 Monochromatic, [OK]
Monochromatic, [OK]